Here’s a crime story with multiple interesting twists. Perhaps the biggest news is this part:
…former Ubiquiti developer, who has reportedly been charged with stealing data and trying to extort his employer while pretending to be a whistleblower.
Pretending to be a whistleblower in order to gain power or extort money is very serious act not least of all because it may undermine all legitimate whistleblowers.
Let me put that a different way, though. There seems to be a trend among staff attacking their employer while claiming protected status because they try to align their personal gain objectives with some greater interest.
I am reminded of people asking me about Tristan Harris’ real oppositional position to Google, as he suspiciously branded himself a whistleblower.
It seems to me he was most upset that he personally wasn’t profiting enough and given more power — to him the wrong people were getting all the money and fame. Thus Tristan charted a course for himself to get far more of that, and is primarily using his experience at Google to become famous and wealthy.
My favorite take-down of Tristan is from his not-very-ethical self-promotional movie pretending to be a documentary:
The film is really designed to showcase Tristan Harris, who probably takes up 1/3 of the screen time. Tristan made his name by being the internal “ethicist” at Google for a little while before setting out on his own to become the high prophet of “internet companies are trying to manipulate us!” But, as others have pointed out, Tristan has a habit of vastly exaggerating things, or being misleading himself. As just one example, highlighted by Antonio Garcia-Martinez in his must-read dismantling of the film, is that Harris argues that we didn’t have these same problems with earlier technologies — like the bicycle. But as Antonio points out, there was, in fact, quite a large moral panic about the bicycle…
I covered this “controversial machine” in my 2019 Keynote called “Whose AIs Are On Your Data“, not to mention for many years before.

Notably, the controversy about bicycles that “revolutionized politics” (pun presumably intended) was related to oppression and freedom of women.
Netflix failing to be in a 2020 Netflix film about companies like Netflix that do bad things, failing to include voices of women, comes across as a giant nail in Tristan’s attempted whistleblower status claim.
Shameless. But this also doesn’t change the fact that someone attacking their former employer may in fact expose them for serious mistakes.
Thus, the second notable point in the Ubiquiti crime story is a turnabout — how a supposed whistleblower has been exposed for making serious mistakes.
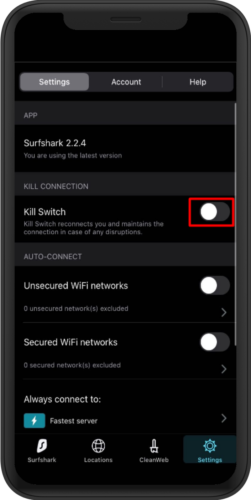
According to the indictment, after securing a job at another company, Sharp allegedly used his still functional privileged access to Ubiquiti’s systems at Amazon’s AWS cloud service to download large amounts of proprietary data. To cover his tracks, Sharp had used a SurfShark VPN connection to mask his real IP address. He then sent a ransom note to Ubiquiti using the same cover, demanding 25 bitcoin in exchange for a promise not to share the data. However, investigators were able to trace the downloads to Sharp because his flaky internet connection briefly failed multiple times, exposing his real IP address. And, he forgot to turn on the Kill Switch on his SurfShark VPN. By default, this is off.
As I said, you can see Ubiquiti exposed for using AWS infrastructure (infamously insecure configurations) leaving privileged access enabled for ex-staff, not to mention allowing massive extractions of data. That’s a lot of oops.
However, far more interesting in this case is Sharp being not so sharp. (They say the only criminals are dumb ones because if they’re smart they never get charged with being criminal.)
He bungled the basics of VPN configuration (likely because impatient, if not just sloppy and incompetant) after he bungled the basics of VPN purchase.
…investigators were also able to link the attacker’s VPN connection to a SurfShark account purchased with Sharp’s PayPal account.
The cost of SurfShark is so minimal, it begs the question why Sharp didn’t think to pay anonymously.
In this case, perhaps we also should ask why SurfShark markets itself for safety online while lacking any warning that it will by default expose your personal information (IP address).
In fact SurfShark warnings go the opposite direction from safety; when you enable the “kill switch” it warns your connection may be protected causing outages. It encourages you to operate less safely for the benefit of smooth connectivity.
“How to use Kill Switch” seems incredibly selfish and misleading of SurfShark (emphasizing better availability and thus fewer support calls, while failing at basic confidentiality — they had ONE job).
Windows:

OSX:

Android:

iOS: