A serious and fresh vulnerability discovered in September led to a notice in November from NETGEAR. As you might expect, that company “strongly recommends that you download the latest firmware as soon as possible”.
Fine. That sounds normal until you consider the totality of vulnerable products versus the ones getting updates (those models under active firmware maintenance are fixed, other models are… uh-oh):
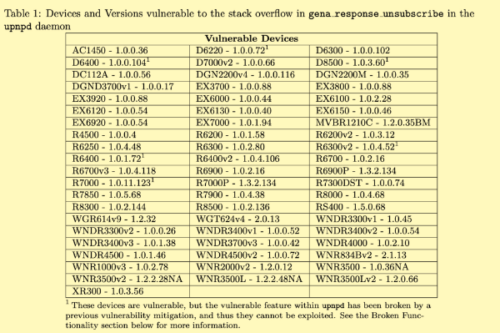
Note that big caveat/footnote from the researcher that a previous NETGEAR fix “broke” GRIMM’s exploit code. An odd perspective on something being fixed for users, calling it “inadvertently broken” for adversaries…
Speaking of perspective, it’s worth noting that perhaps GRIMM smelled blood in the water after NETGEAR had to disclose major issues in March and June.
I mean this kind of attention gathering could help explain why summer months turned into two additional unique September disclosures (1 and 2) before now.
To be fair, 2020 was an even noisier vulnerability banner year for NETGEAR disclosures with 22 unique CVE assigned (mostly XSS).

As bad as all this year’s unauthenticated bypass disclosures sound, still we’re talking UPnP in the latest one. Thus it’s also worth mentioning that Shodan probes give a clear “honeypot” warning for those scanning the globe right now.
