Chris Colotti offers a vCloud Connector 1.5 guide that highlights security
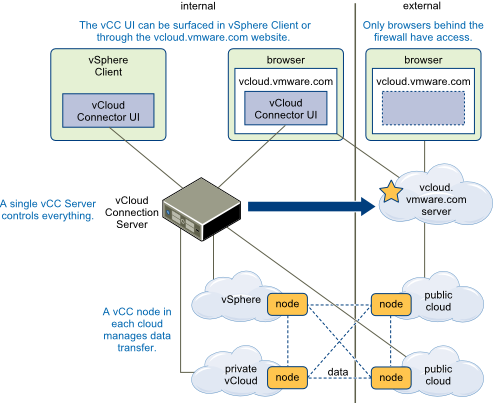
Security – It is important to understand the security of these components. The Server and Nodes communicate over SSL using port 8443 and this is the port used my the online portal to connect to your server. So it stands to reason you will want to generate some real certificates at least for your vCloud Connector server since that will be connected to be the remote nodes as well as the portal. The local nodes may not be as big a concern since they are on the same network. However you can see below, that if you are transferring a workload from a private cloud to the public the two nodes will interface and then you have an argument for some real certificates on all nodes as well. Generally in a production deployment I would get all real certificates, but in my lab I decided not to.
It is great to see this called out but I strongly recommend installing certificates in all deployments (and restriction to communication only over port 8443). In addition, certificate warnings should never be ignored once a new system is configured, as I explained in my presentation at VMworld — Penetration Testing the Cloud.
Vendor (i.e. VMware) default certificates should always be replaced. They do not have to be “commercial CA” certificates. You also can create your own signing certificate offline and use it to sign certificates that you generate. Many do-it-yourself options are available, as long as you carefully protect the signing certificate’s key. Microsoft’s public CA is common in Windows environments. Note that even a hardware security module (HSM) appliance is not very expensive and you of course can still use OpenSSL.
It not only is necessary to use certificates to protect authentication for all your critical systems connected to the network but it also a PCI DSS v2 Requirement.
Requirement 2: Do not use vendor-supplied defaults for system passwords and other security parameters
Malicious individuals (external and internal to an entity) often use vendor default passwords and other vendor default settings to compromise systems. These passwords and settings are well known by hacker communities and are easily determined via public information.
Requirement 2.1 gives a very broad statement that clearly is not limited to production use.
Always change vendor-supplied defaults before installing a system on the network, including but not limited to passwords, simple network management protocol (SNMP) community strings, and elimination of unnecessary accounts.
The VMware product guide for vCC (Installation and Configuration – vCloud Connector 1.5.0) has steps to replace certificates. Note the first sentence mentions production use again. Also note the passwords:
If you have not yet replaced the self-signed certificates in your vCC Server and vCC Nodes, you need to do so before production use.
Procedure
1. Log in to the admin Web console for each vCC instance in which you are going to replace the certificate.
2. For vCC Server, click on the Server tab, SSL button. For vCC Node, click on the Node tab, SSL button.
3. Generate and download a Certificate Signing Request by clicking Generate and Download CSR.
Depending on your certificate authority, you might need to create a new private key before you download the CSR. Contact your CA for more information.
a. If you need to create a new private key, log in to the console of the Server (hcserver) or Node (hcagent) as root. The default password is vmware.
b. At the prompt, change directory to /usr/local/tcserver/springsource-tc-server-standard/server or agent/conf.
c. Delete the existing private key.
/usr/java/jre-vmware/bin/keytool -delete -alias hcserver or
hcagent -keystore tcserver.jks -storepass changemed. Create a new private key.
/usr/java/jre-vmware/bin/keytool -genkey -keyalg RSA -keysize 2048 -alias hcserver or
hcagent -validity 1095 -keystore tcserver.jks -storepass changeme -keypass changemee. Log in to the Server Web admin console and download the CSR as described in Step 1 above.
4. When you have your certificates, upload the root or intermediate certificate from your CA and the new X.509 certificate for your instance by using the two Browse buttons.
5. Locate the certificates on your local machine and then click Upload.
What to do next
Once you have installed the valid certificates, deselect the Ignore SSL Certificate flag in the Node registration window for each Node. See “Register vCloud Connector Nodes with vCloud Connector Server,†on page 32 for more information on this flag. For the change to take effect, you must restart the Server.