Note that some of the most effective armor technology on land and sea uses a porous model.
First, take for example a visionary in World War I realized it’s better to be flexible in order to make breaches quickly disappear (render them ineffective) rather than to try only to prevent them (allow cracks to form in a solid and be exploited). That idea led to self-sealing fuel tanks for aircraft and vehicles.
The US military is still funding research to find ways to use a flexible yet porous membrane to prevent leakage for water tanks as well as fuel. Here is a typical modern breach response study application:
…enable vehicle operation in hostile environments and minimize loss of fuel due to a direct/indirect hit…
Second, another interesting example is a membrane developed on submarines in World War II that can subdue enumeration (e.g. sonar) by an attacker. An anechoic tile is porous enough to allow signals in yet prevent them from a “bounce” back out. Porous sound canceling material also can be found in recording studios.
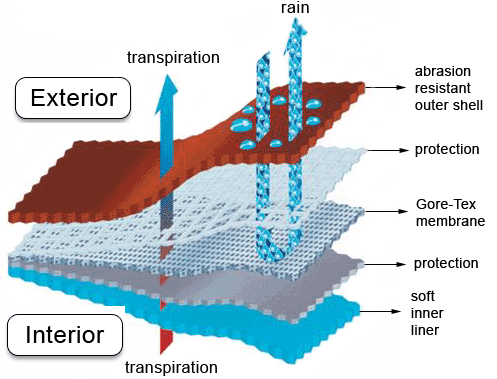
Third, polytetrafluoroethylene (often known for its use in Gore-Tex) is another great example since it is used to make fabric waterproof yet breathable — porous yet impermeable.
I said earlier to take note of the porous model because Wired has offered the following chilling quote in a story called Darpa Begs Hackers: Secure Our Networks, End ‘Season of Darkness’ about the state of American cyber security.
U.S. networks are “as porous as a colander,†Richard Clarke, the former White House counterterrorism chief turned cybersecurity Cassandra, told a packed ballroom.
He says that like being porous is a bad thing. I would rather hear response time is inadequate or that the US needs to develop better tools for the job to distinguish friend from foe (e.g. grapes from water)

Begging hackers to develop a perimeter with no holes, or to imply that a security barrier should never be porous, will trend things worse not better. It would be more effective to spend resources (beg hackers) to help on threat recognition, redirection and response.
A solid perimeter will never be truly solid as history shows time and time again…and again.

To retain and protect assets while dispensing/releasing threats, which is exactly what a colander is designed to do (and why a chef uses one), is not an inherently bad model. As the military examples show above there is a long history of developing highly technical colanders that provide an efficient security solution to handle even the highest risk environments.