This timeline is published by Randori itself, disclosing “authorized use” of a zero-day in Palo Alto products.
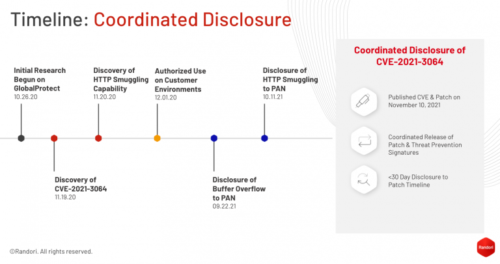
- 2020-10-26: Randori began initial research on GlobalProtect.
- 2020-11-19: Randori discovered the buffer overflow vulnerability.
- 2020-11-20: Randori discovered the HTTP smuggling capability.
- 2020-12-01: Randori began authorized use of the vulnerability chain as part of Randori’s continuous and automated red team platform.
- 2021-09-22: The buffer overflow vulnerability was disclosed by Randori to PAN.
- 2021-10-11: The HTTP smuggling capability was disclosed by Randori to PAN.
- 2021-11-10: PAN released patches and a security bulletin assigning the vulnerability CVE-2021-3064.
- 2021-11-10: This report was published.
CVE-2021-3064 is a buffer overflow that occurs while parsing user-supplied input into a fixed-length location on the stack. The problematic code is not reachable externally without utilizing an HTTP smuggling technique. Exploitation of these together yields remote code execution under the privileges of the affected component on the firewall device. The smuggling capability was not designated a CVE identifier as it is not considered a security boundary by the affected vendor. In order to exploit this vulnerability, an attacker must have network access to the device on the GlobalProtect service port (default port 443). As the affected product is a VPN portal, this port is often accessible over the Internet.
What does this mean? While it’s tempting to focus on the ethics of Palo Alto for “authorizing” behavior, or for the ethics of that behavior… the reality on the ground is Randori has painted a very large target on themselves as a suspicious repository of zero-day information.
In related news of very large targets, even though this sounds like a headline from a decade ago, Sky admits just now that it left 6 million consumer network devices vulnerable for 1.5 years.
…researchers say it took Sky 18 months to address. The vulnerability could have affected anyone who had not changed the router’s default admin password.
The BBC headline really should have been “The Sky is failing” as in Sky was “failing to meet numerous deadlines they set themselves”.

